Section 01 |
The Problem
Your Security Operation Has a Communication Crisis
Every interaction is a bottleneck. Every handoff loses context. Every stakeholder speaks to a different system, or no system at all.

Section 02 |
Communication Agents
Conversational Agents for Every Security Workflow
Purpose-built agents that understand security context, respect operational boundaries, and maintain complete audit trails. Each agent handles a specific domain. All agents share unified intelligence.
Section 03 |
The Architecture
One Conversational Layer. Every Channel. Complete Context.
The Communication Interface sits between your stakeholders and your security operation. It understands who's asking, what they need, and what they're authorized to receive.

Section 04 |
Industry Applications
Communication Designed for Environments Where Failure Isn't an Option
Generic communication tools don't understand matter confidentiality, HIPAA constraints, NERC CIP requirements, or TWIC verification. These agents do.
The confidentiality imperative: When a client speaks their name in your lobby, attorney-client privilege is already at risk. Paper visitor logs expose who has visited. Verbal check-in broadcasts client identity to anyone within earshot.

The dual mandate: Patient privacy under HIPAA. Staff safety in an environment where 75% of workplace assaults occur. Communication systems must serve both without compromise.

The compliance burden: NERC CIP mandates specific communication protocols with 15-minute alert requirements and 90-day log retention. Manual processes can't meet these standards consistently.

The coordination complexity: TSA, CBP, Coast Guard, local law enforcement, port authority—each with separate communication systems. International travelers with language barriers. Time-critical operations where delays cascade.

Section 05 |
Trust Architecture
Enterprise-Grade Conversation. Complete Control.
Security communication handles sensitive information, authorizes physical access, and coordinates emergency response. The architecture must be trustworthy at every layer.
Identity Verification
Multiple authentication factors available per interaction type. Integration with enterprise identity providers. Continuous session verification, not just initial authentication.
Role-Based Response
What the system shares depends on who's asking. A visitor gets wayfinding. An employee gets their credential status. An executive gets incident trends. Same question, authorized answers.
Behavioral Baseline Action Boundaries
Every action type has configurable authorization requirements. Badge issuance: automatic. Temporary access extension: requires host approval. Emergency lockdown: requires authenticated security personnel.
Conversation Encryption
End-to-end encryption for all interactions. Data encrypted at rest and in transit. Customer-managed key options for regulated environments.
Audit Immutability
Every conversation, every decision, every action logged to immutable storage. Tampering detection. Export in standard formats for legal and compliance review.
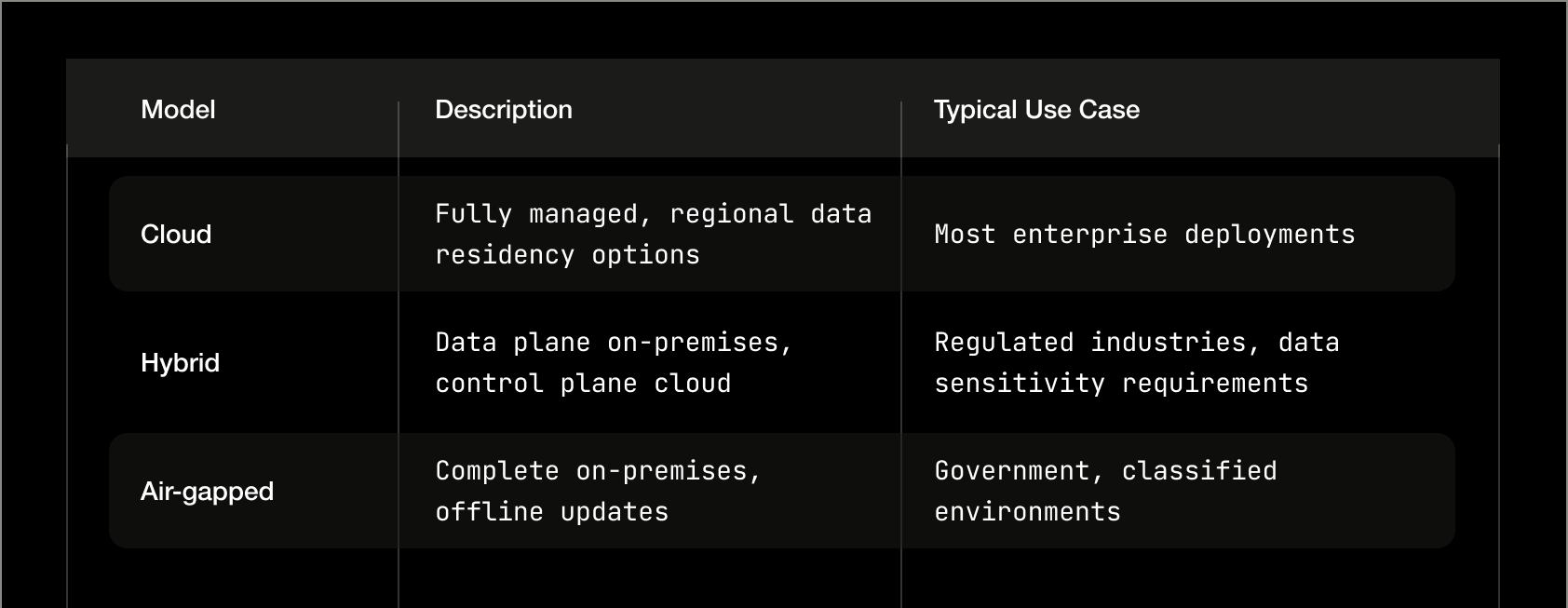
Data Residency
Regional deployment options for data sovereignty requirements. US, EU, Middle East, and APAC regions available. Air-gapped deployment for classified environments.

EU data protection requirements

Annual audit, report available under NDA

Certified information security management

No prohibited components

BAA available for healthcare deployments
Section 06 |
What Changes
When Security Can Communicate
The gap between your security systems and your stakeholders closes. Every interaction becomes an opportunity for security intelligence.

Section 07 |
Integration
Works With Everything You Have
The Communication Interface connects to your existing security systems through the Integration Fabric. No rip-and-replace. No data silos.

Section 08 |
Target Outcomes
What Communication Intelligence Delivers
Measured improvements across visitor experience, guard effectiveness, employee satisfaction, and compliance burden.

Section 09 |
Integration
Works With Everything You Have
The Communication Interface connects to your existing security systems through the Integration Fabric. No rip-and-replace. No data silos.
Assessment
2-3 weeks
Document current communication flows and pain points
Map stakeholder types and interaction patterns
Identify integration requirements
Define authorization policies and escalation paths
Establish success metrics
Configuration
3-4 weeks
Deploy Integration Fabric connections
Configure agent scopes and authorization rules
Develop site-specific conversation content (safety briefings, wayfinding)
Integrate identity systems
Configure channels (kiosk, mobile, Teams, radio)
Pilot
4-6 weeks
Deploy to single site or controlled stakeholder group
Parallel operation with existing processes
Collect conversation logs and failure cases
Refine based on real usage
Train security operations staff
Production
Ongoing
Expand to additional sites/stakeholder groups
Continuous monitoring and refinement
Regular authorization policy review
Incident response procedure updates
Performance optimization
Section 10 |
Honest Positioning
What the Communication Interface Is—and Isn't
We believe in clear expectations. Here's where the Communication Interface excels and where other approaches may be more appropriate.

The Layer Your Security Stack Is Missing
Your video management has AI. Your access control has AI. Your threat detection has AI. Your communication—the thread that connects every stakeholder to your security operation—has been running on manual processes and fragmented channels.
Related resources

Integration Fabric
Your cameras, access control, visitor systems, parking gates, and building management already generate the data. Mithriv's Integration Fabric connects them into a unified layer, without replacing what works.

Intelligence Engine
From connected data to autonomous action. How Mithriv's AI layer transforms integration into intelligence.




.svg)