Section 01 |
The Fragmentation problem
Your Security Stack Generates Data. Mountains of It.
Here's what happens at a typical enterprise campus on a typical Tuesday:
The access control system logs 47,000 badge events. The VMS processes 2.3 terabytes of video. The visitor management system checks in 340 guests. The parking system validates 1,200 vehicles. The room booking platform confirms 89 meetings.
Five systems. Millions of data points. Zero shared context.
When your GSOC gets an alert—unauthorized badge attempt at the datacenter door—the investigation begins. Pull up the access control log. Find the credential. Switch to the VMS. Locate the camera. Scrub to the timestamp. Check the visitor system. Was this person expected? Check the room bookings. Were they supposed to be in this building at all?
Four platforms. Six browser tabs. Twelve minutes. For a single alert.
Multiply by the 200+ alerts your team processes daily.
This is the fragmentation tax. Every enterprise pays it. Most don't realize how much.
The math doesn't work
Average enterprise runs 8-12 disconnected security systems
Incident correlation requires checking 4-6 platforms manually
Investigation time measured in hours, not minutes
Context lost between systems, rebuilt by humans every time
Legacy integration approaches made this worse. Point-to-point connectors that break when vendors update. Middleware that passes messages but doesn't preserve context. PSIM dashboards that visualize fragmentation without solving it.
The Integration Fabric takes a different approach.
Section 02 |
What the Integration Fabric does?
The System of Record for Physical Security
The Integration Fabric ingests events from every source, normalizes them into a common schema, and maintains a live operational model of your entire physical security environment.
Every badge tap, camera motion event, visitor check-in, parking gate activation, and room booking updates the model continuously. When you query the system, you're querying current reality. The last sync cycle is irrelevant because there is no sync cycle.
When a visitor checks in, the Integration Fabric knows their host, their scheduled meeting room, their parking assignment, and their access permissions. When that visitor badges into an unexpected area, the system has complete context without manual correlation.
The Integration Fabric doesn't just read from your systems, it writes back. Credential provisioning, access rule updates, emergency lockdowns, and automated responses flow from intelligence to action through the same unified layer.
Section 03 |
Integration categories
What Connects to the Integration Fabric
The Integration Fabric spans every system that touches physical security and workplace operations. Pre-built integrations deploy in days. Custom integrations scope based on system complexity.
The foundation. Badge events, door states, reader health, access rules, all normalized into the operational model.
Genetec Synergis
HID
Lenel
S2 NetBox
Brivo
AMAG
Gallagher
Paxton
Honeywell Pro-Watch
Software House
Kantech
Keri Systems
PDK
OpenPath
Verkada Access Control
Real-time badge events with credential resolution
- Door forced/held/propped alerts
- Reader online/offline status
- Access rule configurations
- Credential lifecycle (provision/suspend/revoke)
Access events are the highest-fidelity signal in physical security. A badge tap is a verified identity at a specific location at a precise time. The Integration Fabric makes this data queryable, correlatable, and actionable across your entire operation.
Surveillance footage gains value when correlated with operational context. The Integration Fabric links video to events, locations, and identities.
Genetec Security Center
Milestone XProtect
Honeywell MAXPRO
Axis Camera Station
Verkada
Rhombus
Avigilon
Hanwha Vision
Bosch VMS
ExacqVision
Digital Watchdog
Eagle Eye Networks
Arcules
Camera health and status monitoring
- Motion and analytics event triggers
- Bookmark and clip creation
- PTZ preset activation
- Video export for evidence compilation
Video without context requires scrubbing. Video with context becomes evidence. When an access anomaly triggers, the Integration Fabric automatically identifies relevant cameras, timestamps footage, and packages clips for review—what took hours now takes seconds.
Visitor operations touch every part of the security stack. The Integration Fabric ensures visitor data flows where it's needed, when it's needed.
Envoy
iLobby
Proxyclick
SwipedOn
Traction Guest
Kastle
Sign In Enterprise
WorkInSync
plus native Mithriv visitor capabilities
Pre-registration with host validation
- Check-in/check-out events
- Visitor badge credentials (temporary access)
- Watchlist screening status
- NDA and compliance acknowledgments
Visitors create complexity. Temporary credentials, escort requirements, restricted areas, time-bound access. The Integration Fabric manages the complete visitor lifecycle—from registration to departure—with full audit trails and automatic credential expiration.
Space utilization data adds occupancy intelligence to security operations. Know who should be where, and when.
Microsoft 365 / Outlook
Google Workspace
Robin
Skedda
Envoy Desks
Condeco
Teem
Joan
Appspace
WorkInSync
plus native Mithriv visitor capabilities
Room reservation schedules
- Desk booking assignments
- No-show and cancellation events
- Occupancy sensor data
- Space capacity and utilization
Security and space management have converged. When the Integration Fabric knows a conference room is booked for six people but access logs show twelve entries, that's intelligence. When a reserved desk shows no badge-in by 10am, that's operational data for hot-desking policies.
Vehicle access is physical access. The Integration Fabric extends identity governance to parking operations.
SKIDATA
TIBA
HUB Parking
Parkade
ParkOffice
FlashParking
SpotHero Enterprise
INDECT
Custom LPR systems
plus native Mithriv visitor capabilities
License plate recognition events
- Permit validation and violation flags
- Gate open/close commands
- Reserved space assignments
- Contractor and visitor vehicle registration
Parking gates are access control for vehicles. A terminated employee's badge may be deactivated, but is their vehicle still on the permit list? The Integration Fabric enforces consistent identity governance across pedestrian and vehicle access.
Point-of-sale integration adds consumption patterns to the operational model.
Compass Group
Sodexo
Aramark
Toast
Square
Custom cafeteria POS systems
Transaction events with badge/credential linkage
- Meal plan balance and subsidies
- Vendor and contractor meal tracking
- Consumption analytics by location/time
Cafeteria transactions are presence validation. Badge taps at 8am followed by lunch purchase at noon creates behavioral baseline. Anomalies—like a credential used for building access but never appearing in cafeteria or meeting room systems—surface through correlation.
HVAC, lighting, elevators, and environmental controls contribute to security awareness and response.
Johnson Controls Metasys
Honeywell WEBs
Siemens Desigo
Schneider EcoStruxure
Tridium Niagara
BACnet-compatible systems
Modbus endpoints
HVAC zone status and schedules
- Elevator floor access and destination dispatch
- Lighting schedules and override events
- Environmental sensor data (temperature, humidity, air quality)
- Fire alarm and life safety status
Building systems complete the operational picture. Elevator destination dispatch integration means access control extends to floor selection. HVAC schedules inform occupancy expectations. Fire alarm integration triggers coordinated emergency response across all systems.
Bridge physical and logical security with enterprise identity integration.
Microsoft Entra ID (Azure AD)
Okta
Ping Identity
SailPoint
CyberArk
ServiceNow
Workday
SAP SuccessFactors
Active Directory
LDAP
Employee lifecycle events (hire, transfer, terminate)
- Group membership and role changes
- Credential provisioning requests
- Access review and certification
- Incident ticket creation and updates
Physical access should follow the same governance as logical access. When Workday processes a termination, the Integration Fabric revokes building credentials before the employee reaches the exit. No manual workflow. No orphaned access.
Response requires communication. The Integration Fabric connects to every channel your team uses.
Microsoft Teams
Slack
Cisco Webex
Two-way radio systems (Motorola, Kenwood, Hytera)
Mass notification (Everbridge, AlertMedia, Rave)
SMS gateways
VoIP/SIP
Alert routing by role, location, and severity
- Guard dispatch with location and context
- Emergency broadcast across all channels
- Acknowledgment and escalation tracking
- Radio-to-app bridging for field communication
Security operations fail at communication boundaries. The Integration Fabric ensures the right information reaches the right people through the right channel—whether that's a Teams message for an executive escort or a radio dispatch for a guard response.
Section 04 |
Architecture
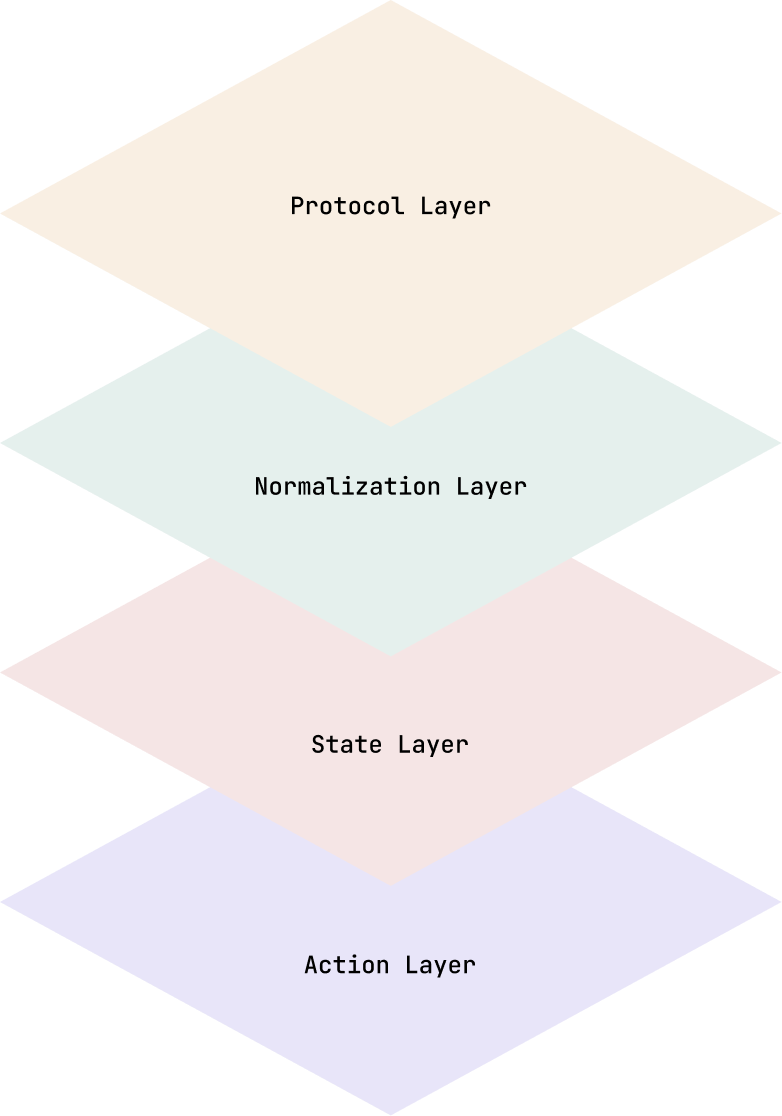
How It Works
Hub-and-spoke diagram showing Integration Fabric at center, with connection lines to eight system categories. Data flows indicated bidirectionally. Mithriv Intelligence Engine shown above the fabric, receiving unified data and sending action commands back through the fabric to source systems.
Protocol Layer
Native support for security industry standards: ONVIF for video, OSDP v2 for access control, BACnet for building systems. REST APIs for modern cloud applications. Legacy protocol adapters for older systems.
Normalization Layer
Raw events from disparate systems transform into a unified schema. A "door forced" alert from Genetec and a "door held open" event from Lenel become comparable, queryable, actionable data in the same format.
State Layer
The operational model maintains current state across all systems. Not just event logs—live understanding of who is where, what credentials are active, which doors are locked, what zones are armed. Updated continuously.
Action Layer
Intelligence flows back to source systems. Lock commands, credential updates, camera presets, elevator recalls—the Integration Fabric doesn't just observe, it orchestrates.
Cloud-connected
Full platform capabilities with regional data residency options (US, EU, Middle East, India). Automatic updates, managed infrastructure, elastic scaling.
Hybrid
Data plane on-premises, control plane cloud-connected. Sensitive data never leaves your network. Policy updates and management through secure cloud interface.
Air-gapped
Complete on-premises deployment for classified or regulated environments. Offline update packages. No external connectivity required.
Section 05 |
Operational Scenarios
Integration in Action
These scenarios demonstrate how unified data enables intelligent operations.
Unauthorized Access Attempt
Visitor Overstay
Emergency Mustering
Section 06 |
Compliance & Certifications
Security Infrastructure Built to Be Audited
We protect security operations for Fortune 500 enterprises and critical infrastructure. That requires a compliance posture that survives scrutiny. Annual audits. Continuous monitoring. Documentation that holds up.

EU data protection requirements

Annual audit, report available under NDA

Certified information security management

No prohibited components

BAA available for healthcare deployments
Section 07 |
Integration Development
Built for Configuration. Extensible by Design
Pre-built connectors deploy in days. Custom integrations build on documented APIs and published schemas. The Integration SDK handles authentication, event normalization, and action interfaces. Your team builds the logic. The platform handles the plumbing.

Pre-built connectors
Deploy with configuration, not code. Typical deployment: 2-5 days per system.

Integration SDK
For custom development. Python and JavaScript libraries. Event schemas, action interfaces, testing frameworks included.

Partner certification program
For system integrators. Training, sandbox environments, and certified integration validation.
Section 08 |
Integration Development
Proven at Enterprise Scale
100+
Enterprise customers
3,000+
Sites under management
22
Countries
80+
Pre-built integrations
1M+
Daily transactions processed
99.99%
Platform uptime




.svg)