Section 01 |
The Response Gap
Millisecond Detection. Minute-Long Response.
Your security stack detects threats in milliseconds.
Your cameras identify unauthorized access at T+0. Your access control logs the badge attempt at T+50ms. Your analytics engine flags the anomaly at T+200ms.
Then the waiting begins.

Section 02 |
The Intelligence Gap
Connected Systems Need Connected Understanding
The Integration Fabric brings your security systems into one operational model. Real-time state across access control, video, visitor management, building systems, and identity.
The Intelligence Engine makes that unified data actionable.

Consider three events within 60 seconds:
- Badge tap denied at server room door (credential lacks authorization)
- Motion detected in adjacent corridor
- Fire door opened in same building wing
The Intelligence Engine correlates: The badge belongs to a terminated contractor whose credentials should have been revoked three weeks ago. The motion is that contractor walking toward an alternative entrance. The fire door is their attempt to bypass access control.Three events. One threat. One coordinated response.
The pattern across security operations:

Section 03 |
The Reasoning Framework
From Detection to Decision
The Intelligence Engine operates through four concurrent capabilities:
Intelligence Capability Framework
Four interconnected nodes that expand when selected, showing detailed capability descriptions and operational examples.
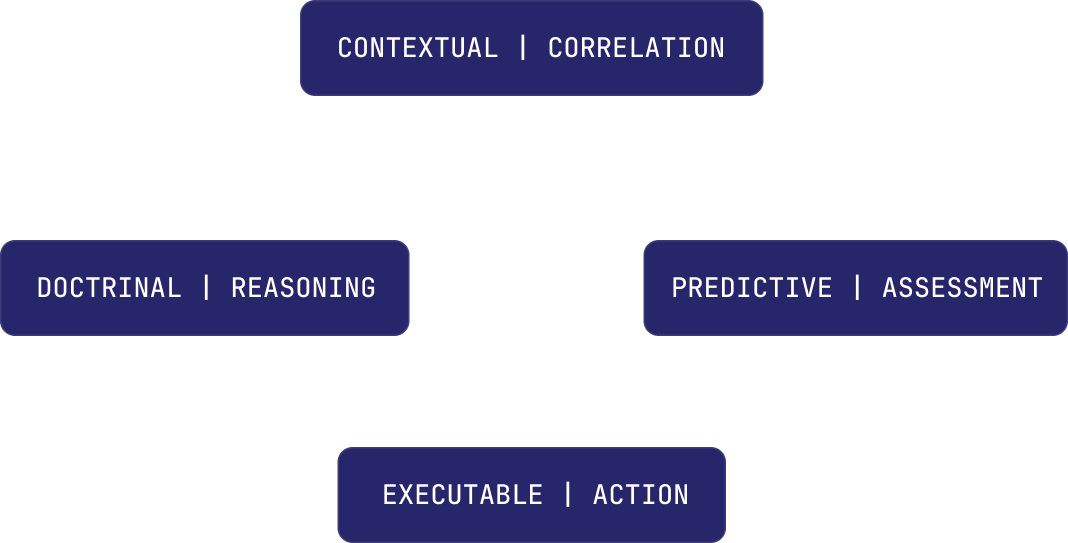
Understanding events in relation to identity, location, time, history, and organizational context.
Example output:
"Marketing director attempted data center access at 2 AM, firstattempt ever at this location, 3 weeks after announcement ofcompetitor job offer. Behavioral deviation score: 94."
Requires:
Real-time state across all systems, identity resolution, behavioral baselines, organizational data
Applying your operational doctrine, SOPs, policies, escalation
paths, to correlated events automatically.
Example output:
"Event matches SOP 4.2.1 (Insider Threat Protocol). Required actions: Notify CISO within 15 minutes, preserve video evidence, document in HR system, do not confront directly."
Requires:
Encoded SOPs, policy hierarchies, exception handling, compliance requirements by jurisdiction
Evaluating threat probability and impact based on patterns
across time, sites, and historical incidents.
Example output:
"Motion pattern consistent with vehicle reconnaissance. Third occurrence this week. Previous incidents preceded theft at similar facilities. Threat probability: ELEVATED. Recommended: Enhanced patrol, law enforcement notification."
Requires:
Historical incident correlation, cross-site pattern analysis, threat modeling, environmental factors
Initiating appropriate responses through connected systems, doors, cameras, credentials, communications, documentation.
Example output:
Guard dispatched via radio with location, video clip of subject, access history, and recommended approach. Relevant doors locked. Cameras tracking. Evidence preservation initiated. Incident record created.
Requires:
Requires: Bidirectional system control, action authorization framework, audit trail, rollback capability
Section 04 |
How the Intelligence Engine Works
Reasoning at Machine Speed. Control at Human Discretion.
The Intelligence Engine is the decision layer that sits atop the Integration Fabric and connects to stakeholders through the Communication Interface.

The Reasoning Core (Can connect to above)
The Reasoning Core processes events from the Integration Fabric through four concurrent analysis paths:
Identity Resolution
Who is involved? Employee, visitor, contractor, unknown? Role, clearance level, normal behavior pattern. Location appropriateness for this identity at this time.
Spatial-Temporal Analysis
Location and timing context. Adjacent space activity. Historical patterns for this location. Facility schedule alignment.
Behavioral Baseline Comparison
Deviation from individual patterns. Deviation from role patterns. Deviation from location patterns. Peer comparison analysis.
Threat Pattern Matching
Known threat indicator correlation. Reconnaissance pattern detection. Social engineering signature matching. Insider threat progression identification.
These analyses complete in parallel. The Reasoning Core synthesizes results into a threat assessment with confidence scores, recommended actions, and supporting evidence, within 600 milliseconds.
The Doctrine Library
Your operational doctrine, SOPs, policies, compliance requirements, encoded as executable logic

The Action Framework
The bridge between decision and execution.
Authorizes
Evaluates whether the Intelligence Engine can execute autonomously or requires human approval, based on action type, confidence level, and configured boundaries.
Executes
Initiates actions through the Integration Fabric: door locks, camera presets, credential updates, guard dispatch, notifications, evidence preservation.
Audits
Logs every decision, every action, every outcome with full reasoning chain. Export-ready for compliance, legal, and insurance.
Learns
Tracks outcomes. When human operators override recommendations, the system captures the correction for supervised learning.
The Learning Layer
Intelligence that improves through operation.

Section 05 |
Graduated Autonomy
You Define the Boundaries. The System Respects Them.
The Intelligence Engine operates within a graduated autonomy model, a progression where you control what executes automatically, what requires approval, and what remains purely advisory.
AUTONOMY SPECTRUM
The Intelligence Engine monitors, correlates, and assesses.All responses require human initiation.
Deployment context: Initial deployment, building trust, highly regulated environments, situations requiring 100% humanaccountability
System executes automatically:
- Correlates events across systems
- Generates threat assessments with confidence scores
- Recommends actions with reasoning
- Prepares evidence packages
- Creates audit documentation
Human role:
- Reviews all assessments
- Decides on all responses
- Initiates all actions
- Validates all outcomes
The Intelligence Engine recommends specific actions withone-click execution. Humans approve before execution.
Deployment context: Standard operations, situations requiring human judgment, actions with significant consequences
System executes automatically:
- All L0 capabilities, plus:
- Pre-stages recommended actions for approval
- Prepares communications for human review
- Queues guard dispatch with full context
- Drafts incident reports
Human role:
- Reviews recommendations
- Approves or modifies actions
- Executes pre-staged responses with single click
- Reviews and sends prepared communications
The Intelligence Engine executes routine actions automatically. Significant decisions escalate for approval.
Deployment context: Mature deployments, well-understood scenarios, time-critical routine responses
System executes automatically:
- Suppress known false-positive patterns
- Route alerts to appropriate queues
- Attach video clips to incidents
- Create standard documentation
- Send routine notifications
Human role:
- Credential revocations
- Physical lockdowns
- External communications
- Actions affecting VIPs
- Novel threat patterns
The Intelligence Engine operates autonomously within definedboundaries. Humans handle exceptions and strategic decisions.
Deployment context: High-volume environments, after-hoursoperations, scenarios with proven playbooks, time-criticalresponses
System executes automatically:
- Complete SOP execution for known scenarios
- Credential lifecycle (provision/suspend/revoke)
- Guard dispatch and coordination
- Evidence preservation
- Compliance documentation
- Compliance documentation
Human role:
- Actions outside defined boundaries
- Low-confidence assessments
- Novel patterns without playbooks
- High-impact decisions
- Policy exceptions
Human focus:
- Exception handling
- Strategic decisions
- Policy refinement
- Relationship management
- Continuous improvement
Simulation Playground
Before any automation goes live, test it.
The Simulation Playground runs your SOPs against historical incidents, synthetic scenarios, and edge cases. See exactly how the Intelligence Engine responds. Identify gaps. Refine policies. Build confidence

What the Simulation Playground reveals:
- SOP gaps: Scenarios your current procedures don't address
- Timing optimization: Where response sequences can be accelerated
- Threshold calibration: Confidence level tuning for appropriate action triggers
- Edge case handling: System behavior in ambiguous situations
- Compliance alignment: Automated response verification against regulatory requirements
Run simulations before deployment. Run them after policy changes. Run them when regulations update.
Section 06 |
Operational Scenarios
What Security Intelligence Delivers
These scenarios demonstrate how the Intelligence Engine transforms specific operational challenges, from VIP management to emergency response.
Section 07 |
Audit-Ready by Default
Documentation That Generates Itself
When every decision flows through a unified intelligence layer, compliance becomes a byproduct of operation.
What the Intelligence Engine provides:
Every decision, every action, every outcome logged with:
Complete reasoning chain
Why the system made each assessment
Evidence linkage
Video, access logs, communications attached
Policy mapping
Which SOP, policy, or regulation governed the response
Timestamp precision
Millisecond accuracy across all systems
Immutable storage
Tamper-evident logging for legal defensibility
Frameworks addressed

Audit preparation

Section 08 |
Clear Expectations
What the Intelligence Engine Is, and Isn't
Where the Intelligence Engine excels:

High-alert-volume environments
where operators cannot process every event manually

Multi-site operations
requiring consistent response regardless of local staffing

Organizations with documented SOPs
that can be encoded as executable doctrine

Environments with integrated systems
providing data for correlation

Operations with compliance burden
where documentation must be comprehensive

Facilities with turnover challenges
where institutional knowledge must persist
Where other approaches may fit better:

Single-site operations
with low alert volume and stable, experienced staff

Organizations without documented procedures
(we can help develop them, but the Intelligence Engine requires operational doctrine)

Facilities with minimal system integration
(Intelligence requires data; start with the Integration Fabric)

Environments requiring 100% human decision-making
for regulatory or policy reasons
The honest tradeoff:
The Intelligence Engine operates within the boundaries of its training data and encoded doctrine. It excels at pattern recognition, correlation, and rapid response within known scenarios. Novel situations, strategic decisions, and sensitive interpersonal matters require human judgment.
Organizations seeking to make their security staff dramatically more effective will see significant returns. The Intelligence Engine amplifies human capability.
What we acknowledge:
Confidence scores, not certainty
Why the The system provides probability assessments and escalates uncertainty.system made each assessment
Continuous improvement
False positives reduce over time through supervised learning; they don't disappear immediately.
Implementation investment
Meaningful automation requires configuration, testing, and organizational change.
Fit assessment
Some environments aren't ready for AI-assisted security operations.
Questions to ask any vendor (including us):
- "Show me the reasoning chain for a decision." The Intelligence Engine exposes how it reached every conclusion.
- "What happens when the system is wrong?" Human override, escalation paths, and learning mechanisms are built into the architecture.
- "How does the system adapt to our specific environment?" Site-specific tuning, behavioral baselines, and localized doctrine.
- "What's the boundary between automatic and human-approved actions?" Graduated autonomy with configurable thresholds.
- "How do we validate before going live?" Simulation Playground for testing against historical and synthetic scenarios.
Section 09 |
From Assessment to Production
Deployment Built for Enterprise Security
Implementation follows a structured path designed for security operations that cannot afford disruption.
Foundation
(Weeks 1-8)
Before the Intelligence Engine, the Integration Fabric must be in place. If you're already connected through Mithriv, this phase validates existing integrations and identifies gaps.
Activities:
Integration audit: Verify data flow from all connected systems
Baseline capture: Establish normal patterns for your environment
SOP inventory: Document existing procedures for encoding
Stakeholder mapping: Identify approval chains and escalation paths
Deliverable: Readiness assessment with gap remediation plan
Doctrine Encoding
(Weeks 8-10)
Your operational doctrine becomes executable logic.
Activities:
SOP translation: Convert procedures to decision logic
Policy hierarchy: Define which policies apply in which contexts
Exception handling: Document how edge cases should be managed
Approval workflows: Encode authorization requirements
Deliverable: Doctrine Library configured for your organization
Simulation & Calibration
(Weeks 10-14)
Extensive testing in the Simulation Playground before any automation goes live.
Activities:
Historical replay: Run past incidents through the Intelligence Engine
Scenario testing: Execute synthetic scenarios across all encoded SOPs
Threshold tuning: Calibrate confidence levels for appropriate action triggers
Gap identification: Find scenarios your doctrine doesn't address
Deliverable: Validated configuration with documented coverage and gaps
Supervised Deployment
(Weeks 14-18)
Go live at L0/L1 autonomy, the Intelligence Engine recommends, humans execute.
Activities:
Production deployment with full monitoring
Operator training on new workflows
Daily review of recommendations vs. actions taken
Refinement based on real-world performance
Deliverable: Production system with validated performance metrics
Graduated Autonomy
(Ongoing)
Systematically increase automation based on proven performance.
Activities:
Performance analysis by scenario type
Autonomy elevation for proven scenarios
Continuous doctrine updates
Cross-site learning activation
Deliverable: Validated configuration with documented coverage and gaps
Deployment Models

Section 10 |
What Intelligence Delivers
Measured Improvement Across Security Operations

Section 11 |
The Decision Layer
Intelligence That Secures Your Physical World
Your cameras see everything. Your access control logs everything. Your analytics detect everything.
The Intelligence Engine correlates across systems, applies your doctrine, and acts, at machine speed, within human control.
Related resources

Communication Interface
Conversational agents for visitors, employees, and security teams. See how unified communication completes the operational picture.

Integration Fabric
Your cameras, access control, visitor systems, parking gates, and building management already generate the data. Mithriv's Integration Fabric connects them into a unified layer, without replacing what works.




.svg)